If you haven’t heard, Elastix, which was once considered a permanent and trusted fixture in open source VoIP, is no longer a thing.
At least, not in the way it traditionally existed. It is now a product of 3CX, which is a good serviceable platform, but it is not the Elastix we all knew and loved. It now joins Trixbox, as the dearly departed.
What’s going on with Elastix?
 Elastix was one of the first platforms I tinkered with when I first discovered the strangely interesting world of VoIP, and I really liked what it offered. It has a built-in mail server, instant messaging, calendar, CRM, fax server, and of course an Asterisk phone system. It was built on top of FreePBX, which had been a supporter of Elastix for many years. With that said, it never really stood on its own legs. It sported its own user interface, but under the hood sat a somewhat dated version of FreePBX, and of course Asterisk.
Elastix was one of the first platforms I tinkered with when I first discovered the strangely interesting world of VoIP, and I really liked what it offered. It has a built-in mail server, instant messaging, calendar, CRM, fax server, and of course an Asterisk phone system. It was built on top of FreePBX, which had been a supporter of Elastix for many years. With that said, it never really stood on its own legs. It sported its own user interface, but under the hood sat a somewhat dated version of FreePBX, and of course Asterisk.
Elastix entered a rapid decline after FreePBX version 13 was released almost a year ago, which was a true re-definition of FreePBX and raised the bar for open source telephony. The lack of updated to Elastix (other than cosmetic), left those interested in deploying an open source phone system seeking alternative solutions. While the Elastix software remained functional, Sangoma proved its ability to commercially support its software, and release timely updates and patches.
Before going any further, I’d like to address any confusion on IP PBX appliances since some of my posts encourage cloud based hosting versus on-premise appliances. There are several factors that some use to dictate whether or not you should host your phone system in the cloud or use an appliance. The usual two are CapX and OpX, and which best fits with organizations. The dirty truth about modern IP phone systems is that they are incredibly inexpensive when compared to systems 10 to 15 years ago. With that said, it’s fairly cheap to use an appliance on-premise which saves you recurring costs and also Internet bandwidth, which might be a game changer for those with limited options when connecting to the Internet (assuming using SIP trunking). There is, of course, another device to maintain, power, and keep cool, but since the CapX is very low, it may be worth it for you.
Conversely, the advantages of a cloud hosted system are apparent, with convenience being a top benefit, but you will always have that monthly expense. You can, of course, migrate from one platform to another (with software like FreePBX) if you find that a particular solution works better for you. Truthfully, I like both solutions for different situations, but for this posting, we’ll be talking about appliances.
Renegade PBX Mini and FreePBX
 For those of you looking to migrate from Elastix, or even start fresh, I’d like to introduce to you the Renegade PBX Mini from VoIP Supply. The Renegade Mini is a purpose-built appliance with the small to medium size businesses in mind. It can support up to 100 SIP extensions and 75 concurrent calls. It’s also paired well with Sangoma’s FreePBX, which can ship on the Renegade Mini directly from VoIP Supply.
For those of you looking to migrate from Elastix, or even start fresh, I’d like to introduce to you the Renegade PBX Mini from VoIP Supply. The Renegade Mini is a purpose-built appliance with the small to medium size businesses in mind. It can support up to 100 SIP extensions and 75 concurrent calls. It’s also paired well with Sangoma’s FreePBX, which can ship on the Renegade Mini directly from VoIP Supply.
Inside the Renegade Mini, there’s a dual-core Atom processor, 2 Gigs of memory and SSD storage. It also includes one Gigabit Ethernet port, HDMI out, VGA out, and four USB ports, and one PCI-E port fo telephony cards.
The Renegade Mini can be ordered with various telephony cards with FXS, FXO, and T1 interfaces, so it can use your existing telco connection (FXO, T1) while also fully supporting SIP trunking. A major benefit to the Renegade Mini is that there is a very low total cost of ownership. Essentially, the software is free (utilizing FreePBX), which does not require any licensing, and does not impose any limitations on things like the number of extensions that can exist, or concurrent calls. The only limitations are hardware resource based. FreePBX does offer commercial modules, which you pay for, but none of them are required to have a fully functional system.
As of last week, Sangoma has released a Conversion Tool to help with migration from Elastix (with FreePBX 2.9 or newer) which can save you a lot of time and effort, especially if you were not the one who originally configured the system.
VoIP Supply can also help you migrate from one system to another (even if you are not coming from Elastix), or even provision a brand new deployment for you for an additional charge. If you’re new to VoIP and want to hit the ground running with an appliance-based solution, reach out to VoIP Supply and they’ll be happy to take care of you.
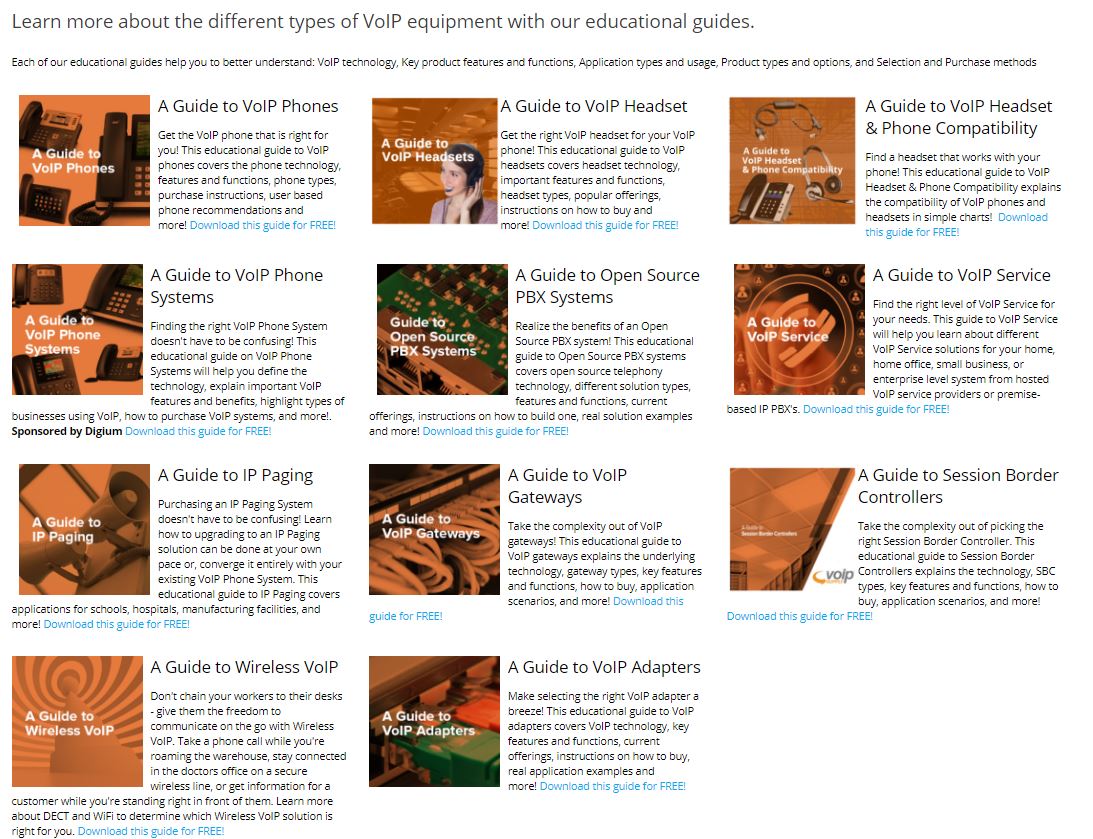
 To make your learning experience even better, we have updated some of our VoIP guides. Follow the links below to find the four updated VoIP guides:
To make your learning experience even better, we have updated some of our VoIP guides. Follow the links below to find the four updated VoIP guides:




 The Grandstream GXV 3240
The Grandstream GXV 3240
 The Polycom VVX 500
The Polycom VVX 500

 Elastix
Elastix




 The IP 560
The IP 560













