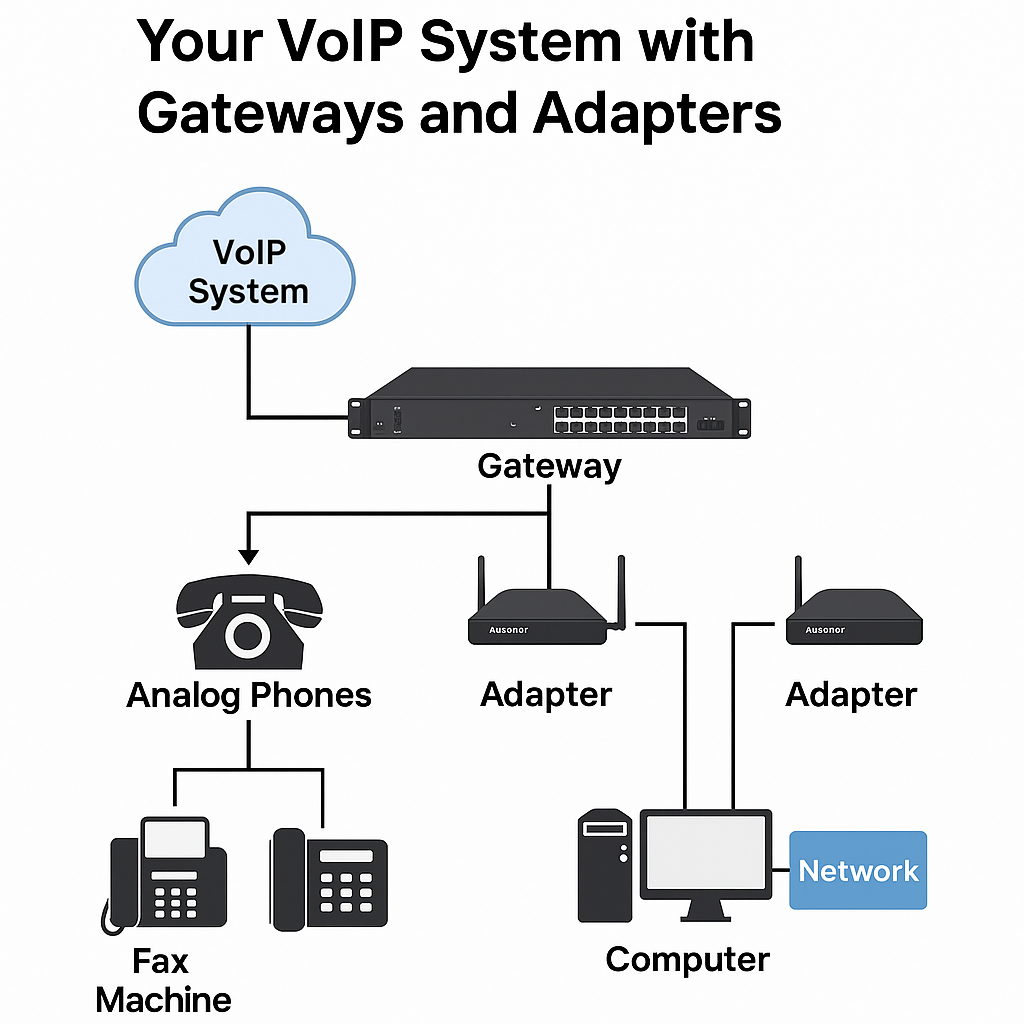
How To: How to Expand Your VoIP System with Gateways and Adapters

Growing pains don’t only happen to people, they happen to businesses too! It’s fantastic that your business is growing! What is not so fantastic are the growing pains a business owner can experience from quick or excessive growth. One of these pains can be communication needs. If you are already using a VoIP system, no need for a whole overhaul or a new system. If you are working with legacy infrastructures or maybe have analog devices, no worries! Fortunately, there are devices made specifically to help bridge this gap and scale your network. VoIP gateways and analog telephone adapters (ATAs) make it easy to expand your network. Let’s take a look at what these are and how they can help you with your growing pains!
First, let’s make sure we know exactly what VoIP gateways and adapters are. VoIP gateways are devices that convert analog voice signals to digital data for transmission over an IP network. They come in two main types:
- FXO Gateways: Connect to the Public Switched Telephone Network (PSTN) to bring traditional phone lines into your VoIP system.
- FXS Gateways: Connect analog devices like fax machines, intercoms, or desk phones to your VoIP network.
Analog Telephone Adapters (ATAs) are smaller devices that connect individual analog phones or fax machines to a VoIP system. They’re ideal for smaller deployments or when you only need to integrate a few legacy devices.
Download the VoIP Supply Gateways Guide to learn more about these!
Download the VoIP Supply Adapters Guide to learn more about these!
There are several scenarios in which you may want to consider using VoIP gateways or adapters.
- Continue to use analog phones while migrating to VoIP.
- Paging systems utilize analog, and you don’t want to replace them.
- Support for analog fax machines.
- Multiple locations with legacy infrastructures.
- Integration of traditional phone lines (PSTN) for backup or hybrid communications.
Whichever scenario may apply to you and your business, you should start by assessing your current infrastructure. Ask yourself questions like:
Which analog devices or PSTN lines are still in use?
How many endpoints will need connection?
You will then want to select gateways or adapters based on the number of ports required, compatibility with your VoIP platform, power options, and mounting requirements.
See below for various options from popular brands sold at VoIP Supply!
Grandstream 48 FXS Port Gigabit Analog Gateway GXW4248-V2: Enables cost-effective hybrid IP and analog phone systems for any business size. It supports 16 to 48 FXS ports, offers Gigabit connectivity, and ensures compatibility with most SIP platforms.
Patton SmartNode 4141 4 FXO Analog Gateway SN4141/4JO4V/EUI: Bridges old and new technology, making it ideal for integrating legacy phones or fax machines into modern All-IP networks. It offers interfaces, service transparency, and flexibility.
AudioCodes MediaPack 5xx analog VoIP Gateway with 8 FXS Voice Interfaces TAA MP508/8S/SIP/TAA: Connects up to eight analog devices to a VoIP network with secure SIP support and high voice quality. TAA-compliant and easy to deploy!
Yeastar NeoGate TA1610 16 FXO Gateway: A 16-FXO gateway fully compliant with SIP and IAX2, offering echo cancellation for up to 128 delays. It supports PnP, DHCP provisioning, TR-069, and SNMP, and includes a 3-year Yeastar warranty.
Sangoma Vega 60GV2 4 Port FXO Media Gateway: Connects legacy phone systems to IP networks, ideal for SIP trunking, IP Centrex, and IP phone survivability. Supports up to 4 analog or BRI lines (12 calls), SIP, T.38 Fax, and offers local survivability during outages.
Mediatrix C733 8 FXO Gateway – TR-069 Enabled C733-01-MX-D2000-K-001: business-class analog VoIP gateway featuring 8 FXO ports and 2 10/100 Ethernet ports, designed to connect your VoIP system to the PSTN.
Poly ATA 400 1FXS VP SIP VoIP Adapter US 8F3H4AA#ABA: Poly ATA is a device that is configurable to work with any SIP-compliant internet telephone service (ITSP).
Cisco ATA 191 Adapter ATA191-K9: Has two standard FXS ports, which can be configured independently as two Session Initiation Protocol (SIP) registrations. Protect and extend existing investments in analog systems.
It may all sound a bit confusing, but if you take away anything from this information, just know that you can save time and money by utilizing gateways and adapters to expand and scale your network without breaking the bank on a whole new system overhaul. Our VoIP Experts are here to help! If you have any questions or comments, you can leave them below, call us at 1-800-398-8647, or chat with one of our VoIP Experts online at www.voipsupply.com.